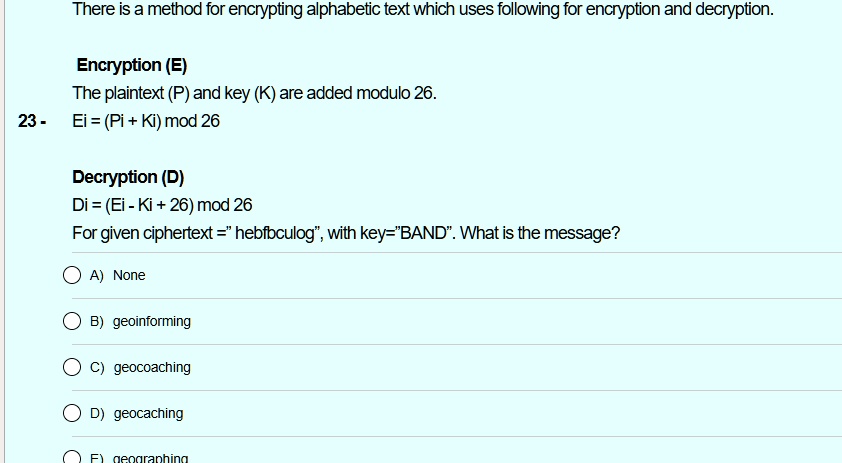
SOLVED: There is method for encrypting alphabetic text which uses following for encryption and decryption: Encryption (E) The plaintext (P) and key are added modulo 26. 23 - Ei = (Pi +

Encryption and decryption Process of Vigenére cipher Description: Pi =... | Download Scientific Diagram

Implementation of Vigenère Cipher on Raspberry Pi Pico C++ : 9 Steps (with Pictures) - Instructables
![The Original 26 × 26 Vigenere table [13]. The encryption equation (E)... | Download Scientific Diagram The Original 26 × 26 Vigenere table [13]. The encryption equation (E)... | Download Scientific Diagram](https://www.researchgate.net/publication/342474014/figure/fig1/AS:906657022345216@1593175287161/The-Original-26-26-Vigenere-table-13-The-encryption-equation-E-for-a-Vigenere.jpg)