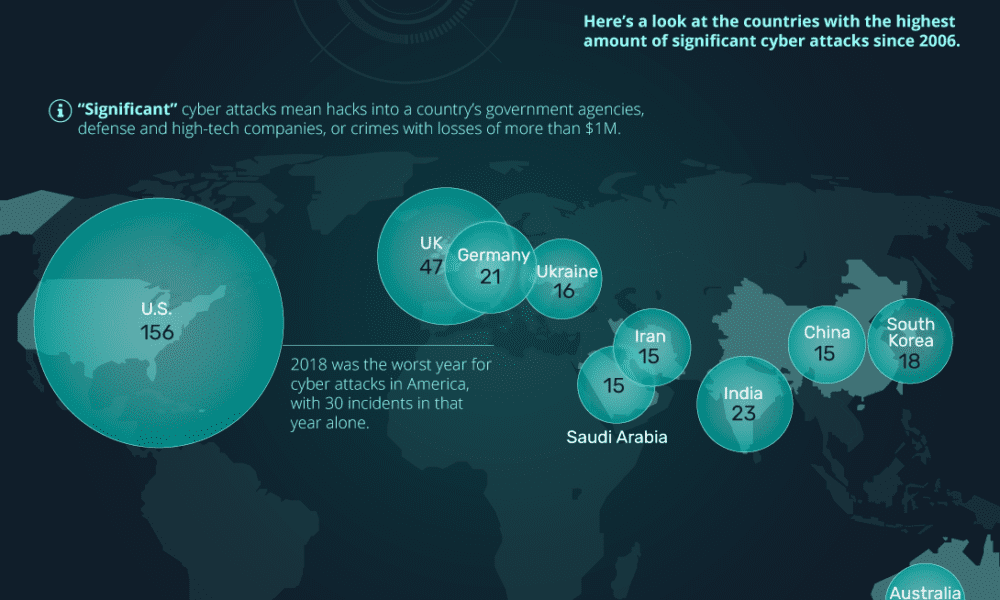
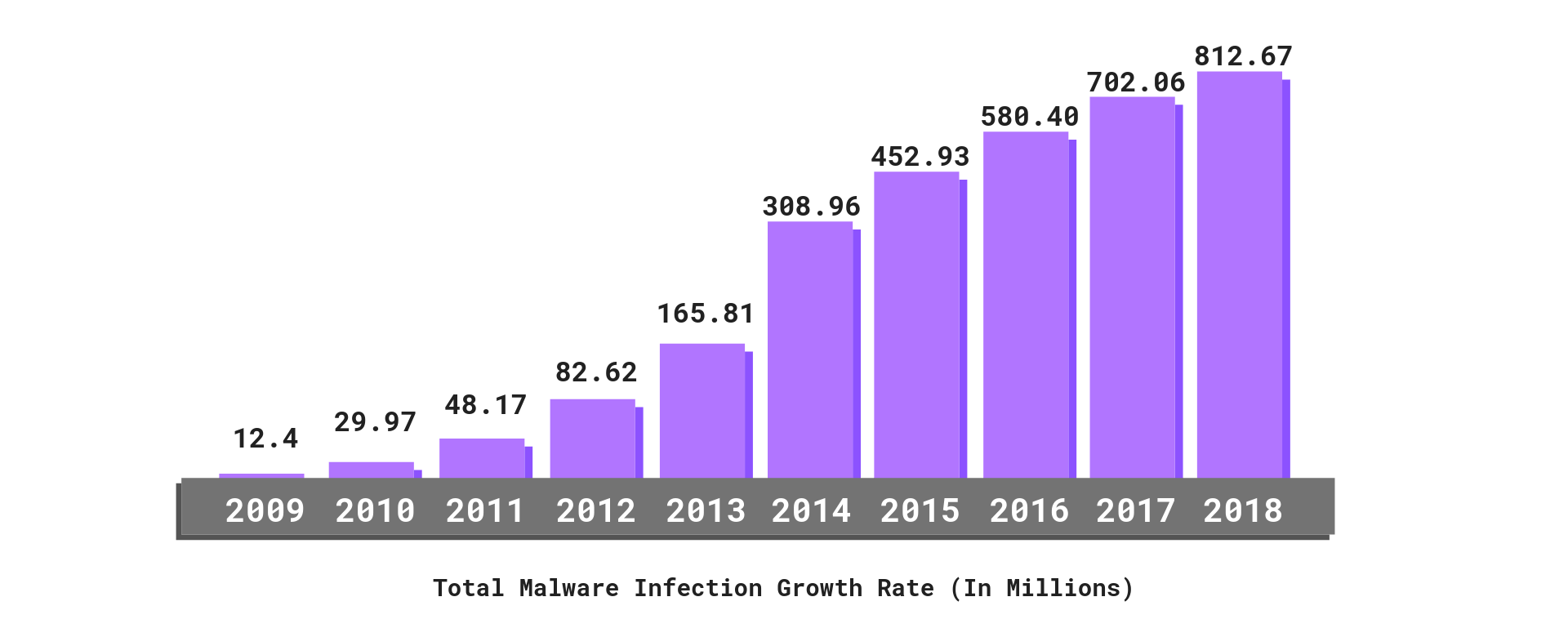
A coordinated nation-state cyber attack is a worst-case scenario, says former U.S. chief technology officer

PDF) Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic | Harjinder Lallie - Academia.edu

Cyber Case Study: SolarWinds Supply Chain Cyberattack - Ollis/Akers/Arney Insurance & Business Advisors

Morning brief: Over 670k cyber attack cases in India this year so far | Latest News India - Hindustan Times

Code Injection Cyber Attacks: How They Work | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More
Cyber Attack Case Study Ppt Powerpoint Presentation Visuals | Presentation Graphics | Presentation PowerPoint Example | Slide Templates